1. Project Overview
Security parameters are considered as the variables that can help in analysing the input as well as output factors so that an evaluation can be made. Security parameters have been designed and implemented in a way that it can help in managing the information and data including all the functions and operations in an order that it can stay away from any sort of risk or threat (Kizza, 2017). In every company, there is a specialised and private amount of data that can be attacked by any external party, so for managing the security concerns of the company, these security parameters can provide an efficient range of help in providing efficient security concerns to Info tech Pty Ltd. The project is about analysing the understanding of knowledge required to implement the security parameters and also to verify whether the firewall is acting efficient and able enough for the policies made by Info tech Pty Ltd.
Increase Your Odds of Success With Our
- Scholastic academic documents
- Pocket friendly prices
- Assured reliability, authenticity & excellence
2. Client Overview
Info tech Pty Ltd is one of the leading IT companies that deal with a variety of services and processes for various business and home purposes as well. It involves enormous number of IT services and they provide the same to various parties for completing their projects and services. But the fact that is to be ensured here is that due to the lack of expertise, the company was not able to implement security measures and that is the reason they had to take help from the outbound sources for having an efficient rate of the security of the network (Kerznerand Kerzner, 2017). But in case of this, there are some risk factors associated that the personalised set of data and information of Info tech Pty Ltd can get leaked or stolen because of any third party. So, it is better if Info tech Pty Ltd makes the implementation of the security parameters on their own so that they can be able enough to have a proper control over it. This will help them in achieving a sort of efficiency in the whole functioning because they can be able to monitor if any factor is not going appropriate enough. IN that case, they can make the modifications and improvements as soon as possible.
3. Scope
The project is supposed to focus on the analysis of knowledge and skills that are essential for developing all security parameters of Info tech Pty Ltd. although for completing the security concerns, the company is relying on some outside partners that provides them help for providing security measures. There is an actual requirement of the security measures in Info tech Pty Ltd because their enterprise network is small enough and also, the internet is connected with the help of a small router. Therefore, scope of the project is to implement efficient knowledge and skills so that appropriate security parameters can be implemented in Info tech Pty Ltd in order to tackle the security concerns on their own.
4. Project assessment report
4.1 Introduction
The key issue of project is that Info tech Pty Ltd has a small enterprise network. In that network, internet is connected with the help of a small router. So, this might create some complications for Info tech Pty Ltd. There are no as such security policies developed and implemented by Info tech Pty Ltd because the organsiation lack in the expertise of it. This is the reason they have taken some sort of support from outside partners. They are responsible for making all the security decisions for them. Info tech Pty Ltd is IT company which provides enormous number of IT services for various purposes such as for home as well for business related purposes etc. Therefore, there is actually the need of security parameters that they can implement on their own. By this way, they will not have to stay dependent on any of the external factors or parties. Info tech Pty Ltd have made a policy and to investigate whether it can act feasible enough to be implemented, a firewall has been set up. Also, for checking the compliance, an audit has also been performed.
4.2 Project findings
For completing of the requirements of project, which is to make the implementation of the security concerns by the company itself, they will be needing some security parameters to implement so that they can have an efficiency for sharing to public services from internet as well. Therefore, rather than depending on the external sources for security concerns, Info tech Pty Ltd has decided to make the involvement of security parameters on their own and also to check whether firewall can be able to investigate that the policy developed is accurate or not. Info tech Pty Ltd can ensure following the internal as well as external connectivity requirements so that they can be able to decide that what are the factors that they need to implement. It will complete the implementation of the perimeter security. Some internal and external connectivity requirements are discussed as following :
Internal connectivity requirements
Performance and redundancy needs
Investigating about the performance of the network and the security parameters associated with it is important enough. It is because this is very important to check that whether all the parameters are acting accurately and are in a way that Info tech Pty Ltd can be able enough to manage the new implementation itself without the involvement of any outbound source etc. for coping with the security needs and requirements of the company.
External connectivity requirements
Addressing the needs
It is obvious that when Info tech Pty Ltd will implement security parameters, there must be a variety of factors that they need to implement along with that. Some of the well known examples of the factors involve cost, other required resources etc. So, this is obvious that along with the network, Info tech Pty Ltd have to cover the requirements of other important measures such as cost etc. as well. Also, Info tech Pty Ltd have to design virtual private networks as well. The configuration of the VPN in Info tech Pty Ltd will help in extending their network from private to public as well. Also, by such means, the employees of Info tech Pty Ltd will be able to share all their data and information to other systems as well that are connected over the network, whether private or public (Shan and Liao, 2016). In terms of performance and quality of service as well, Info tech Pty Ltd can make sure to check and investigate the fact that whether the processing is being done in an effective way or not. For this, VPN checks and tests can be implemented by Info tech Pty Ltd that whether it is safe from any unauthorised access or not. It is important to check because cyber criminals are keen to attack the popular industries to get their personalised set of data and information. Therefore, it is important to ensure the external connectivity requirements so that Info tech Pty Ltd may not have to face any sort of complication or issue with their implemented network and security parameters.
Also, as Info tech Pty Ltd is one of the leading IT companies, so there is a huge requirement of maintaining the security measures and parameters in a way that they can be able to protect their data and information. It is because obviously there will be an enormous amount of data that they want to secure from any sort of unauthorised or external access. Therefore, they want a higher level of security in their organisation. It is important as well because they are dependent on some external partners for security concerns etc. But in this case, there may be the risk of some sort of discrepancy etc. that any mid party if in case leaks the personalised amount of data of Info tech Pty Ltd, so it is better if they can develop and implement a security parameter system of their own.
4.3 Recommendations
After a successful implementation of the network and security parameters, there are some aspects that Info tech Pty Ltd may have to consider for making improvements in the perimeter's security and these are discussed as under :
- It is important if Info tech Pty Ltd ensures the actual factors that they think are important and can be attacked by the cyber criminals. So, for protecting their data from that, they can properly identify their access points. It is important to consider because these points are actually the ones which Info tech Pty Ltd should consider and provide security in a way that the hackers cannot be able to have any access on these access points.
- Also, after a proper and successful implementation of the project, Info tech Pty Ltd can understand and analyse that the type of traffic, which is currently going on the network. It is important because it will help them in analysing that what type of attack is attacking them at the time of data lost or stolen (Link, Cordray and Ginter, 2017). So, for that first, they should be aware of the network traffic that is currently running on their network.
- Also, Info tech Pty Ltd can ensure involving a wide range of the security tools that are specialised and advanced that they are un hackable. By this way, their network can stay protected from any sort of unauthorised access. Therefore, it is very important if Info tech Pty Ltd develops a range of security tools while the implementation of the security perimeter's. By involving a range of tools that cannot be hacked, Info tech Pty Ltd will even ensure that their data and information can stay secured enough. Also, it will help Info tech Pty Ltd to gain the trust of the employees as well. It is because every employee wants that their data can stay safe and secure enough so that any third party etc. cannot have access to the same. This helps in building trust of the employees on the company.
- As there are enormous number of firewalls and some of the well known examples of it can be considered as application firewalls etc. Therefore, an essential step for Info tech Pty Ltd is that they can make involvement of the leveraging firewalls because by such means, they can be able to know effectively about the viruses, worms and hackers as well. Therefore, they can be able to implement ways so that they can stay protected from them. Also, there are various types of risks as well that are associated with firewalls. A fact that is to be ensured here is that it is sensitive enough, so it should be programmed in a way that it can act capable enough for competing with the viruses and risks.
- Segmentation of the areas that are actually endangered, which means that there are various aspects involved such as business applications, videos, browsing, history, VoIP etc. So, if a proper segmentation will be made by Info tech Pty Ltd, then they can easily make involvement of efficient factors that can help in providing security to every single segment. This can also provide enormous benefits to Info tech Pty Ltd in order to maintain the functioning of the security parameters that have been added.
- Along with the security tools, Info tech Pty Ltd can also implement high level security tools. There are enormous number of high level security tools and some common examples of it includes proxy servers, SSL decryption devices, detection techniques etc. The fact that is to be ensured here is that for a successful implementation of the advanced security tools, it is important that a proper segmentation has been already done in Info tech Pty Ltd. Then only, they can make the involvement of the implementation of the advanced security tools so that they can be able enough to design and implement the security parameters for the enterprise's ICT network (Perlman, Kaufman and Speciner, 2016
- Info tech Pty Ltd can also make implementation of the tools by which they can be able enough to capture all the data and the traffic so that on that basis only, they can be able to make effective changes and modifications. A proper visibility over the new network implemented and the security parameters involved, they can be able to analyse properly that what is going over the network. So, this can also eb considered as a major factor that Info tech Pty Ltd can implement so that they can be able to achieve a sort of effetiveness in the whole functioning of the network. It will be very beneficial for them because there are cyber criminals with advanced range of technologies so they can attack the personalised data and information of the company and make any modifications according to them. So, it is very important that Info tech Pty Ltd can make sure to implement a wide variety of these tools so that no sort of complication or issue can affect the functioning and operations of Info tech Pty Ltd.
4.4 Possible OHS concerns
OHS refers to the occupational health and safety. It means that Info tech Pty Ltd have to ensure that all the data and information of the employees in the organisation is safe enough. So, there might be the possibility that some OHS issues can occur, so Info tech Pty Ltd can consider this fact and ensure to implement a number of ways so that they can protect the security and safety concerns of the employees. The final approval can be taken from the management of the Info tech Pty Ltd about the objectives that whether they are effciient enough or not and if there is some sort of discrepancy etc., it can be replaced as soon as possible.
5. Project Analysis and Design
5.1 Project Estimated duration
For completion of the whole project, it is important to consider some factors that acts essential for the project and some common and well known examples of it can be considered as cost, time etc. So, the basic estimation of time will be divided in phases. First phase will be the implementation of the network on its own and developing a wide range of the security parameters so that they cannot rely on outbound sources for establishing internet measures. There, the first phase will be the implementation of the security parameters, then the second is by making it in a way that it can be accessed over public services as well and Info tech Pty Ltd can achieve this by implementing virtual private networks. Then the third phase is that after the development of the whole policy, firewalls can be used for investigating the fact that whether the processing is going in an effective way or there are some factors that needs to be modified. Therefore, this has been analysed that the project might take about 33 days.
|
Phases |
Time duration |
|
Implementation of the security parameters |
12 days |
|
Access over public services |
8 days |
|
Implementation of firewall |
13 days |
|
TOTAL NO OF DAYS |
33 days |
So, it has been evaluated that the estimated duration of the project will be about 33 days which will be involving security paramenter, its implementation, verification of firewall and factors associated with it etc. This is important to analyse because it helps in providing scheduling about the other functions and factors associated.
5.2 Target audience
The target audience for this project will be the whole enterprise network of ICT in Info tech Pty Ltd. As employees play a major role in performing in the operations of the company, so the employees of Info tech Pty Ltd will also act important part of the target audience. IT is important as well because the employees must be aware of the changes that are going to be performed by the company regarding the functioning and processing of the internet on their own. Initially, they were depending on the outbound sources for having internet services, so all the decisions also were made by them. But now as the security parameters will be implemented by their own. So, the employees and the staff should be aware of the ways of implementing and using the same. It is important as well because Info tech Pty Ltd is itself an IT company providing a variety of services to the businesses and for home purpose as well. Therefore, after the implementation of the security parameters, if some issue occurs, if the employees and staff will be able to understand its processing, then they can make modifications and improvements in it as well.
5.3 Mock up design
Mock up design is considered as a framework or model that is being used for analysing the evaluating the whole design of the model. Along with the designing of the model, it also considers the functioning of other processes as well and some well known examples of it includes demonstration, presentation etc. So, after the implementation of the security parameters in the Info tech Pty Ltd, a mock up design for the same can be implemented.
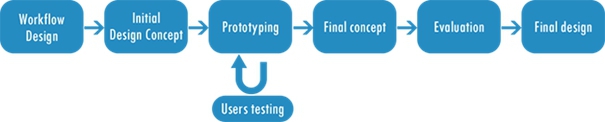
Illustration 1: Mock up design for implementation of security parameters
6. Project Management
6.1 Evaluation of technologies
It is obvious that after the implementation of the security parameters, there must be some hardware and software technologies involved. So, the evaluation of the same is discussed as under :
Software requirements
It is very important to check the software requirements so that it can be very efficiently analysed that the software's of all the security parameters have been implemented in a way that no factor of it can act as a barrier or challenge for it (PHILLIPS, CBAPand PMP, 2018). Whether it is about the functional or the non functional requirements, it should cover all these because this helps in ensuring the fact that the whole processing of the functions and operations is being done in an effective way.
Hardware requirements
It is very important that Info tech Pty Ltd should ensure that all the hardware's for the security parameters have been successfully installed. It is important to ensure that because it can help in further analysing that whether it will throw any impact on the processing or not. Therefore, it is very important to consider all the hardware requirements of the security parameters in order to have an effectiveness in all the functions and operations.
6.2 Project timelines
|
Planning |
Duration |
Start |
Finish |
Predecessors |
|
Investigating an efficient topic for the research |
1 day |
Mon 11/23/18 |
Mon 11/23/18 |
|
|
Analysing the aim along with the objectives |
1 day |
Tue 11/24/18 |
Tue 11/24/18 |
3 |
|
Time scale for an efficient collection of resources |
1 day |
Wed 11/25/18 |
Wed 11/25/18 |
4 |
|
Implementation |
||||
|
Evaluating the themes |
1 day |
Thu 11/26/18 |
Thu 11/26/18 |
5 |
|
Analysing and implementing the aspects accordingly. |
1 day |
Fri 11/29/18 |
Fri 11/29/18 |
8 |
|
Calculating the involved cost |
1 day |
Mon 11/31/18 |
Mon 11/31/18 |
8 |
|
Analysis and interpretation of data |
1 day |
Tue 11/31/18 |
Tue 11/31/18 |
9 |
|
Evaluating the overall findings |
1 day |
Wed 11/31/18 |
Wed 11/31/18 |
9 |
|
Project closure |
||||
|
Understanding the conclusion and recommendations |
1 day |
Thu 11/25/18 |
Thu 11/25/18 |
11 |
|
Gathering the results |
1 day |
Fri 11/26/18 |
Fri 11/26/18 |
13 |
|
Submission of final outcomes |
1 day |
Mon 11/29/18 |
Mon 11/29/18 |
14 |
6.3 Budget
The budget for the project of the implementation of the security parameters for Info tech Pty Ltd is being provided as below :
|
Particulars |
January |
February |
March |
April |
May |
June |
|
Research |
||||||
|
Identifying the cost |
5000 |
10146 |
452 |
5632 |
789 |
6532 |
|
Sales revenue |
16000 |
2562 |
78956 |
80535 |
3265 |
3330 |
|
Other income |
2000 |
2000 |
2000 |
1455 |
4521 |
452 |
|
Total cash inflows |
23000 |
14708 |
81408 |
87622.12 |
8575 |
10314.3 |
|
Cash outflows |
||||||
|
Image editing |
4654 |
384.3 |
11843.4 |
12080.268 |
489.75 |
499.545 |
|
Video editing |
2000 |
6598 |
6598 |
8956 |
4512 |
8952 |
|
Development |
2200 |
2288 |
2380 |
2475 |
7854 |
3652 |
|
Testing |
4000 |
4000 |
4550 |
4550 |
4550 |
4550 |
|
Total cash outflows |
12854 |
13270.3 |
25370.92 |
28060.9688 |
17405.75 |
17653.545 |
|
Cash deficit / surplus or closing cash balance |
10146 |
1437.7 |
56037 |
59561 |
-8831 |
-7339 |
6.4 Copyright and legal issues
When Info tech Pty Ltd will implement a whole new network designing by involving all the security parameters, they will create a whole new design. Unlike before, when they were taking help of the outbound sources for developing an internet connection. It was because they were lacking in the expertise, so they were dependent on the external sources for implementation of the internet connection. So, they can register their network so that no third party can be able to develop the same. It is because Info tech Pty Ltd has involved all the software as well as hardware requirements in a way that has made the whole functioning successful enough. So, it is important to ensure that no external body can be able to take the rights of the same. Therefore, it is important to analyse all the legal factors associated with the copyright. The company, Info tech Pty Ltd is responsible for every single image and content that has been discussed in the report because all the factors are associated with it. It involves all the important aspects such as hardware requirements, software requirements, recommending factors, evaluation and analysis of technologies etc. (Harrisonand Lock, 2017). So, all the rights are with the company itself. No sort of copyright from any other organisation is allowed.
7. Project Sign Off
|
1. Summary of the project |
|||
|
Initial Date of the project |
|||
|
Overall duration of the project |
33 days |
||
|
2. Goal of the project |
|
The goal of the project is to develop a wide understanding of all the skills and knowledge about the implementation of a new network by involving all the security parameters. Therefore, it covers all the hardware, software and other functional requirements necessary for the achievement of all the targets and goals. |
|
3. Deliverables of the project |
|
The deliverables of the project were that a network has been implemented covering all the major aspects such as security parameters etc. So, all the security parameters essential have been included in the implementation of the network. |
|
4. Any other comments |
|
The whole research for the project has been done in an effective way. The information has also gathered successfully and then is being used in the research rpoeprly. |
|
5. Signatures of the document |
||||
|
Name |
Description |
Signature |
Date |
|
|
ABC |
By signing this document, I acknowledge that I have received all the stated deliverables at the agreed to quality levels. |
|||
|
XYZ |
By signing this document, I acknowledge that I have delivered all the stated deliverables at the agreed to quality levels. |
|||
|
Others (if needed) |
||||
Avail of assignment help service from professional experts of Instant Assignment Help Australia.
We believe in serving our customers with the most reliable assignment help
Students Also Like: Children Development and Physical Growth
REFERENCES
- Harrison, F. and Lock, D., 2017.Advanced project management: a structured approach. Routledge.
- JOSEPH. PHILLIPS, P.M.P., CBAP, I. and PMP, C., 2018.PMP PROJECT MANAGEMENT PROFESSIONAL STUDY GUIDE. McGraw-Hill Education.
- Kerzner, H. and Kerzner, H.R., 2017.Project management: a systems approach to planning, scheduling, and controlling. John Wiley & Sons.
- Kizza, J.M., 2017.Guide to computer network security. Springer.
- Link, D.F., Cordray, C.G., Chart, R.M. and Ginter, K., SCIENCELOGIC Inc, 2017.Management techniques for non-traditional network and information system topologies. U.S. Patent 9,537,731.












